Meaningfulness of Penetration Tests
Now that we know how to classify a penetration test, the question remains how meaningful a simulation of such an attack really is if total security is nothing more than wishful thinking. To answer this question, we must first take a look at the word ’security’. The public at large views security as a fixed state. For example, how many times have you been asked whether an IT system is secure? There can only be one answer: not secure. But argumentum a contrario, this doesn’t mean that the IT is wide open to attack. It only means that the question in and of itself is poorly devised. Instead of asking whether or not, the question should be how secure an IT system is, as there is no absolute security. As you probably already noticed, this formulation reveals that security is not a condition but a process. This means the guiding principle is that the more effort invested, the more securely an IT system can be developed or tested within the scope of what we are talking about. The meaningfulness of the penetration tests therefore correlates with the amount of time invested by the penetration tester.
When juxtaposing meaningfulness and the time spent, total security cannot be exceeded, only approximated. In mathematical terms, this is subject to limited growth, which is illustrated in the following diagram.
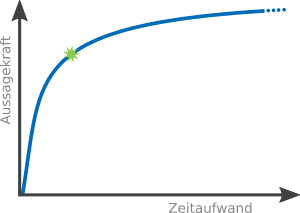
The diagram reveals another important fact: the curve increases as fast as it decreases. From a pentester’s perspective, we can quickly make a statement as to whether a system is catastrophically vulnerable or not when examining an IT system. This requires little more than searching for known vulnerabilities of the installed services on the internet. A more in-depth analysis requires significantly more time though. We may endeavour to autonomously find unpublished vulnerabilities and create corresponding programs for their exploitation. In theory, we could spend an entire lifetime carrying out a single penetration test. But under normal circumstances, we will estimate the effort so that we can make at least one statement on as to whether our target system is built and developed upon a professional level of security or not. This relationship is indicated by the green star in our diagram, which is based on the Pareto principle. It states that 80% of the results can be achieved with 20% of the overall effort.
It is thus part of the job of each penetration tester to provide an estimate as part of the tendering process. The rule is, of course: the more information available, the more accurate the estimate. Consequently, fixed efforts generally do not exist in penetration testing. This must be agreed with the client.
To summarise, penetration testing at a minimum identifies all easy-to-discover vulnerabilities (low-hanging fruits), thus rendering all attacks on the level of a script kiddie harmless. Because of this, the effort exerted by the attacker would increase in line with the effort made by the pentester. A poignant penetration test offers a clear and meaningful statement as to whether a target system or a target application has been principally built or developed on a professional security level.

Write down the amount of time that you have spent in training to perform penetration tests for Dubius Payment Ltd. These may be useful as reference values for comparable estimates. An estimation can possibly be provided through a network description and a brief look at the DMZ network of Dubius-Payment Ltd.
Pentest Training
Take a look at the pentest training chapters and learn penetration testing:
- Preface
- Introduction
- Legal Framework
- Hacking vs. Penetration Testing
- Classification
- Meaningfulness of Penetration Tests
- Penetration Testing Standards
- The Hacking Guide
- Hacking I: Scanning networks
- Hacking II: Password attacks
- Hacking III: Web application attacks
- Hacking IV: Privilege Escalation
- Hacking V: Tunnelling Techniques
- Hacking VI: Vulnerability scanner and penetration testing frameworks
- Demonstration of a Penetration Test
- Risk Assessment of Identified Vulnerabilities
- Structure of Documentation and Reporting
- Insider stories: Tales from Dubius Payment Ltd.
binsec academy GmbH - Online IT Security Training with Practical Focus
binsec academy GmbH is provider of online IT security training, offering practical, lab-based courses for professionals. The academy provides hands-on training in areas such as penetration testing and secure software development. Participants gain practical experience through realistic lab environments, including simulations of company networks and applications. Courses are available in multiple programming languages and align with standards like OWASP Top 10 and PCI DSS. Upon successful completion, participants receive certifications such as the Binsec Academy Certified Pentest Professional (BACPP) and Binsec Academy Certified Secure Coding Professional (BACSCP), demonstrating their ability to identify and remediate security vulnerabilities.
Goto binsec acadmy GmbH

binsec GmbH – Experts in Penetration Testing
binsec GmbH is a German IT security company focused on professional penetration testing. With over 10 years of experience, the team conducts in-depth penetration tests on networks, web applications, APIs, and mobile apps. Certified experts systematically identify and document security vulnerabilities to support organizations in improving their security and meeting compliance requirements.
Goto binsec GmbH