Hackers are unpredictable. Under normal circumstances, their identity or the number of attackers who are targeting a given company remain unknown. This is why potential clients ask for a penetration test to secure their system. But frequently, the scenario of how the simulated hacker attack should be undertaken remains unclear during the client’s initial enquiry. It is therefore our job to classify the penetration test together with the client.
We must always remember that we take on the role of a hacker when carrying out penetration tests. The role of an attacker may be a recently terminated head of IT who seeks revenge against his former employer, or it may be an unknown attacker who is looking for financial gain. To plan a penetration test, we need to know the initial situation and clarify the following questions:
To answer all of these questions, the Federal Office for Information Security (BSI) drafted the “A Penetration Testing Model“. This document provides the following illustration for the classification of penetration tests, among other things:
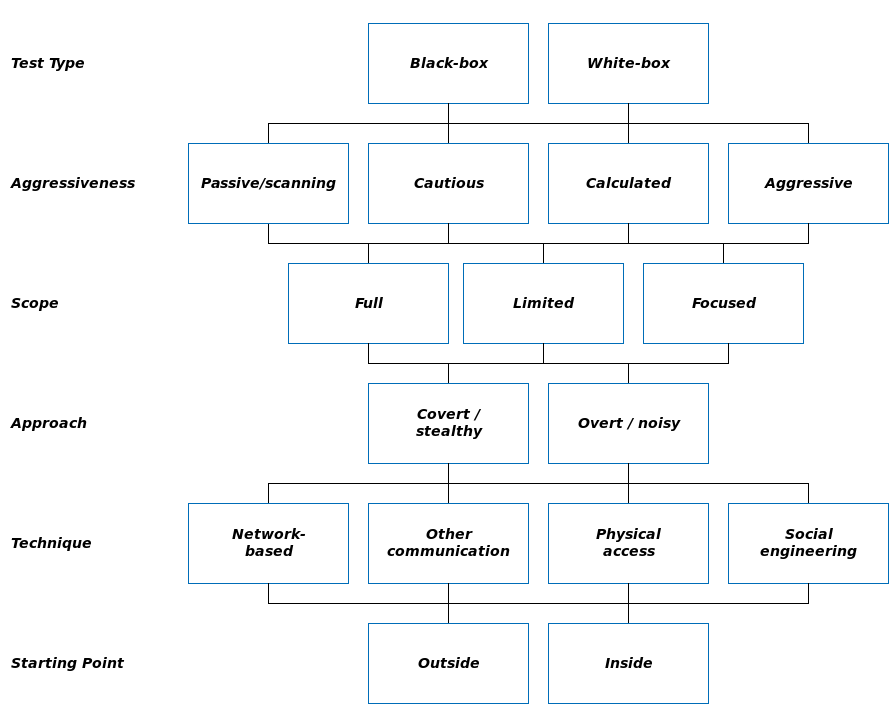
Using these criteria, we can run through the above-mentioned scenario of the fired head of IT, for instance. Unlike a hacker, an IT manager will be familiar with the internal structures and processes of a company, meaning that he will be armed with more information for the attack (white box). This person will also know the applications and systems that he himself was responsible for implementing. Obviously, this gives him a much broader range of attacking options compared to an attacker with no prior ties to the company (full scope). Due to his termination, he will likely act aggressively in order to cause as much damage as possible. He probably won’t care whether his actions will destroy entire systems (aggressive), which means that his actions will probably be discovered sooner or later (obvious approach). But because he was stripped of his access rights as part of his termination, he must resort to accessing the data externally (technique and starting point).

Classify your hacking attack against Dubius Payment Ltd. as described in the above example and explain your choice. The individual classification criteria are described in detail in the BSI document “A Penetration Testing Model“ in Chapter 3.4.
Last modified: Dec. 15, 2022
Take a look at the pentest training chapters and learn penetration testing:
Discover the world of penetration testing. Learn how to infiltrate networks and successfully penetrate systems and applications. Acquire the necessary hacking skills and use them when conducting professional penetration tests. Become a real penetration tester. Here you will find the free documents for the Pentest Training of binsec academy GmbH. The binsec academy GmbH offers the corresponding security training lab environments and certifications. However, the knowledge and wiki articles on hacking and penetration testing is universal.
binsec academy GmbH is the European provider of online security training with virtual laboratory environments. The core component of all security training is the focus on practice, practice and more practice. In the wiki here you will find the public and freely available course materials. You can put the theory into practice at binsec-academy.com.