Dear participants,
Welcome to our online “Pentest Training” course. Before you start stretching your fingers and rolling up your sleeves, we would like to say a few words about this course.
As a penetration tester, you will face the exciting challenge of performing security analyses of IT systems. As you might imagine, penetration testing (pentesting) cannot be learned from books alone. But on the other hand, penetration testing does also require some theoretical knowledge before you can get started. For these reasons, the course consists of the ideal ratio of theory (about 20%) and practice (about 80%):
The most important part of the pentest training is the virtual laboratory environment. This is represented by the fictitious company Dubius Payment Ltd., which you will be allowed to compromise from the perspective of an attacker.

Our documents will demonstrate how this is performed in practice. These documents are split up into chapters and are structured commensurate to how a penetration test is carried out. For this reason, we recommend you work through the individual chapters in the order provided. Of course, you are free to use the documents any way you wish if you prefer, as you know your learning behaviour best. You can continuously track your progress through small multiple-choice tests. As previously mentioned, the chapters only provide the tools, whilst external standard documents or publications on the Internet are referenced for more in-depth knowledge. In our experience, self-generated knowledge is much quicker and easier to sustainably retain rather than presented material.
The virtual lab can be accessed via our OpenVPN server. To do so, you must first schedule your lab start date in your MyPortal via our binsec-academy platform:
Once your personal lab has been fully created, you can download your VPN configuration in your MyPortal and use the openvpn
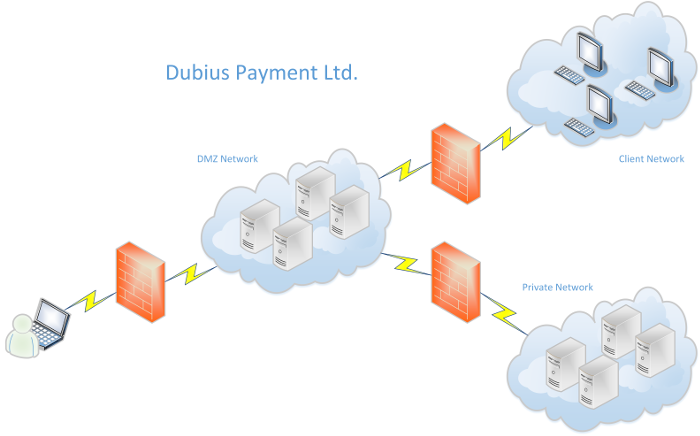
The IT infrastructure of Dubius Payment Ltd. comprises a total of three networks: the DMZ network, the client network and the private network. However, the two internal networks only allow connections to and from the DMZ network and are separated from each other by firewalls. Your job will be to successfully compromise the systems in the DMZ network (10.250.53.0/24) and penetrate the other networks from there. What makes our fictitious company Dubius Payment Ltd. unique is its employees, who may be found on social media and who interact with the IT systems of our virtual lab.
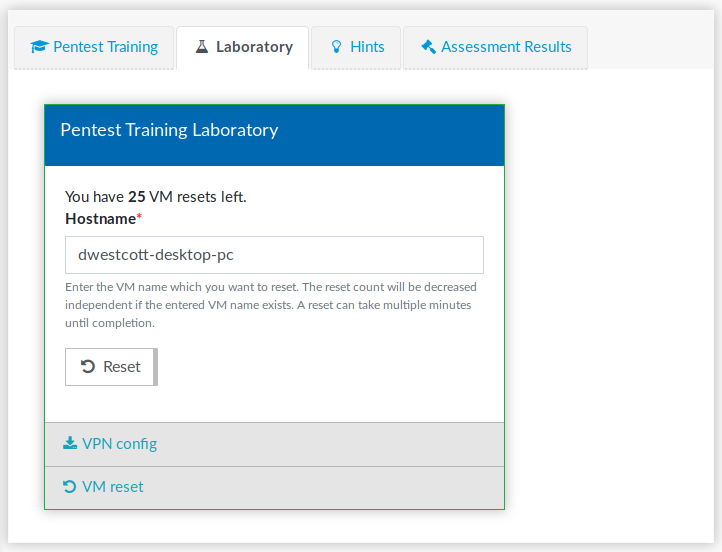
When exploiting vulnerabilities, the function of the target system may be impaired or completely destroyed, among other things that can happen. But to ensure that you get to try all the techniques in the practice lab without having to worry about this, you may reset individual servers based on the domain names in your MyPortal using a limited number of VM resets. For example, if you want to restore dwestcott-desktop-pc.dubius-payment.com to its original state, simply enter dwestcott-desktop-pc in the following entry mask:
VM resets act as a safeguard against a failed exploit, but they do not help you to compromise a target system. Before you start pulling out your hair looking for vulnerabilities, we would like to refer you to our help system. This is where you can unlock tips about the individual IT systems, providing you with concrete attack vectors. Spoilers not only ruin the fun for film and TV, but they also lessen the sense of achievement in compromising an IT system. This is why you can only use a limited number of tips, because our help system is tied to the Academy Coin: each time you wish to use a Joker, you must cash in Academy Coins. To this end, we have set up 100 Academy Coins as starting balance, which can be increased by solving our multiple-choice questions in the chapters.
Generally speaking, each IT system in the lab has been assigned an IPv4 address from the private IPv4 network 10.0.0.0/8 so that this network is routed through our VPN server. If you also obtain IPv4 addresses from the above network range for your work network, you may need to create more specific routes to ensure proper function.
You may use Kali Linux for the attacker machine. Kali Linux is a free penetration testing and security auditing Linux distribution (derived from Debian, based on Debian testing), which includes more than 300 penetration testing tools and pre-installed services. The ISOs or the pre-built VMs can be downloaded here. Of course you are free to use a different operating system for your attacker machine. In that case, all you need to do is install the tools listed.
Last modified: Dec. 15, 2022
Take a look at the pentest training chapters and learn penetration testing:
Discover the world of penetration testing. Learn how to infiltrate networks and successfully penetrate systems and applications. Acquire the necessary hacking skills and use them when conducting professional penetration tests. Become a real penetration tester. Here you will find the free documents for the Pentest Training of binsec academy GmbH. The binsec academy GmbH offers the corresponding security training lab environments and certifications. However, the knowledge and wiki articles on hacking and penetration testing is universal.
binsec academy GmbH is the European provider of online security training with virtual laboratory environments. The core component of all security training is the focus on practice, practice and more practice. In the wiki here you will find the public and freely available course materials. You can put the theory into practice at binsec-academy.com.